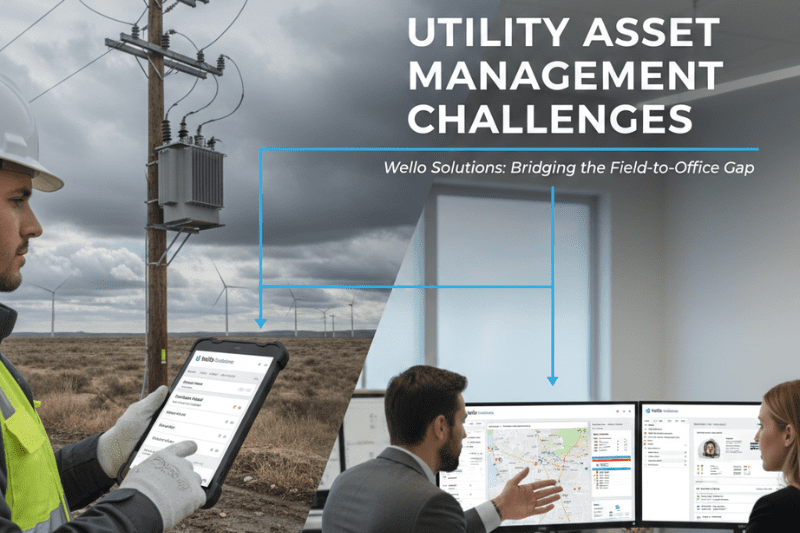
A practical approach to protecting customer data, building trust, and staying ready for audits
Service businesses run on information. Every work order contains customer details. Every asset record includes site data. Every technician update can include photos, notes, signatures, and timestamps. In modern field service, data is not a side output. It is the product of daily operations. That is why data protection and GDPR compliance matter so much for organizations that manage work in the field.
GDPR is often discussed as a legal topic. But for service and maintenance businesses, it becomes very real and very operational. A single mistake can expose customer data, reveal sensitive site information, or create uncertainty about who accessed what and when. That can trigger complaints, contract risks, delayed billing, and damaged trust. Strong GDPR practices do not only reduce regulatory risk. They protect the relationship with customers and help the business operate with confidence.
This article explains GDPR compliance in a way that makes sense for field service and asset-based businesses. It focuses on what a good platform and good operational habits should provide. It also explains what to look for when selecting a field service solution that supports data protection without slowing down teams.
GDPR compliance is a daily workflow issue, not a one-time project
Many organizations approach GDPR like a checklist they can finish once. In reality, compliance is ongoing because operational reality changes constantly. New technicians join. New customer sites are added. New subcontractors receive access. New integrations are connected. New photos and job notes are uploaded. The data footprint grows every day.
That is why a sustainable GDPR approach needs structure and consistency. You want a system that makes the right behavior easy. You want controls that are built into daily work instead of being treated as extra administration. You want traceability so that when someone asks what happened to a piece of data, you can answer quickly, clearly, and accurately.
For a field service business, the challenge is not that people want to do the wrong thing. The challenge is that people are busy, mobile, and working under time pressure. Compliance has to survive that reality.
GDPR REQUIREMENTS
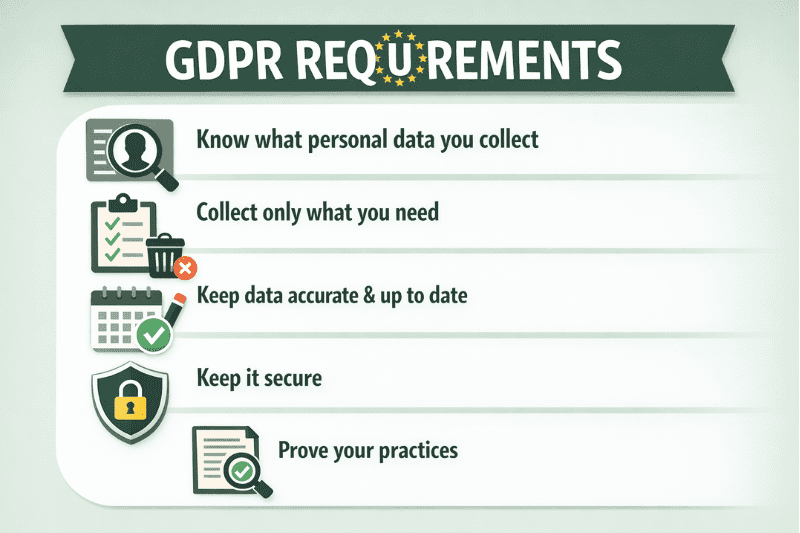
What GDPR requires in practical terms
GDPR is designed to give people more control over their personal data and to push organizations toward responsible handling. In a service environment, this includes customer contact data, addresses, emails, phone numbers, and sometimes signatures or photos where individuals are identifiable. It can also include employee data when staff information is stored or tracked in the system.
At a practical level, GDPR forces companies to answer a few recurring questions:
You must know what personal data you collect and why you collect it.
You must collect only what you actually need.
You must keep it accurate and up to date.
You must not keep it longer than necessary.
You must keep it secure.
You must be able to prove you do these things.
That last part is often where companies struggle. Having intentions is not enough. You need evidence. Evidence usually comes from system design, clear processes, and traceable records.
Why field service and asset-based businesses face unique GDPR exposure
Many industries process personal data. Field service is different because data moves constantly between office and field, across devices, across sites, and often across subcontractors. It is also tied to physical locations and real-world operations, which can create additional sensitivity.
A field technician can view customer details on a mobile device. They might take pictures of equipment that accidentally capture people in the background. They might write notes that include personal information that was not necessary to record. They might download documents and store them locally. They might work offline and sync later. They might work in shared environments like workshops or depots.
These realities increase risk. But they also create opportunities. If your field service platform is designed properly, it can remove a large portion of human error by controlling what is accessible, what is stored, what is logged, and what can be exported.
The foundation of compliant operations is data ownership and visibility
A strong GDPR posture starts with a simple principle. The customer controls their data, and the service organization must be able to see and manage what data exists.
In a practical system, this means you can identify where personal data is stored, who can access it, and how it flows between modules. It also means you can support customer requests without chaos. If someone asks what data you have about them, you should be able to locate it. If someone asks to correct it, you should be able to update it. If someone asks for deletion and you have no legal reason to keep it, you should be able to remove it safely without breaking operational records.
For service businesses, the difficult part is that operational history matters. You cannot always delete everything because maintenance history can be required for warranty, safety, or financial reasons. A good GDPR approach is about controlled retention and proper separation between what must be kept and what can be removed.
A platform that supports this well gives you visibility and control, not uncertainty.
Access protection is where most businesses win or lose
GDPR compliance is not only about policies. It is about preventing unauthorized access. In field service, access protection must work across roles, locations, and devices.
A platform should support role-based access control so that each person sees only what they need. Dispatchers should not automatically see everything across the company if they only manage one region. Technicians should not access customer lists that are unrelated to their jobs. Subcontractors should not access internal information that is not required to complete assigned work. Management should have visibility without forcing broad access permissions for everyone else.
Strong access protection also includes multi-factor authentication, secure password policies, and session controls. If a phone is lost, the device should not become an open door. If credentials are compromised, extra layers should reduce the chance of takeover.
This is not about distrust. It is about reducing blast radius. Most security incidents become serious because access was wider than necessary.
Monitoring and traceability are what make compliance credible
Many organizations claim they protect data. Fewer can show exactly what happened when a question is raised.
Monitoring matters because GDPR expects accountability. In practical terms, accountability means you can answer questions like:
Who accessed this customer record.
Who exported this report.
Who changed this contact detail.
Who approved this action.
When did the change happen.
From which device or session.
A platform that supports logging and audit trails makes this possible. It turns compliance from “we think we are safe” into “we can prove what happened.”
For service businesses, audit trails also help operational quality. When changes are traceable, teams work more carefully. Disputes are easier to resolve. Internal investigations are faster. Customer trust improves because you can answer questions without guessing.
Secure infrastructure is important, but it is only part of the story
Organizations often focus on where data is hosted, which data centers are used, and which security standards apply. Those things matter. They help protect availability, resilience, and baseline security. But GDPR compliance is broader than hosting.
Even with strong infrastructure, a business can still fail on GDPR if access is uncontrolled, if data is exported without oversight, if retention is unmanaged, or if staff do not understand basic handling rules.
The best approach is layered. Secure infrastructure plus secure application design plus controlled workflows plus operational discipline.
Built-in security features should be standard, not optional add-ons
A modern field service platform should provide security capabilities that are built in, not bolted on.
Role-based access should be part of the core design.
Authentication options should support stronger login methods.
Encryption should protect data in transit and data at rest.
Permissions should be granular enough to reflect real job roles.
Mobile access should be controlled and revocable.
Sensitive actions should be restricted and traceable.
When these are built in, compliance becomes a normal outcome of normal use. When they are missing, compliance turns into manual workarounds that rarely scale.
Preventive threat detection and rapid response reduce real-world damage
No system is immune to threats. The goal is to reduce likelihood and reduce impact.
That means detecting abnormal activity early, prioritizing issues based on risk, and responding quickly when something looks wrong. It also means having clear processes for incident handling.
For field service organizations, time matters because operational data moves fast. If an incident affects technician access, the workday can collapse. If an incident affects customer data, trust can collapse. A mature approach balances security response with operational continuity.
It also aligns with GDPR expectations around breach notification. Organizations need to be able to investigate quickly, understand scope, and communicate responsibly.
What “partnering for compliance” should look like in practice
If you use a software provider to process or store personal data, you are not alone in compliance. Roles exist on both sides. Typically, the service company is the data controller because it decides why and how data is used. The software provider often acts as a data processor because it provides the system that processes data on behalf of the controller.
In practical terms, this requires clear contractual commitments around data processing and security responsibilities. It also requires clarity about sub-processors, data handling practices, retention, and support during incidents.
A strong partnership is not about marketing statements. It is about clear documentation, practical controls, and predictable support when customers need answers.
Key capabilities to look for in a GDPR-ready field service platform
If you are selecting or reviewing a field service solution, the most useful approach is to evaluate the platform against practical compliance outcomes. Below are the capabilities that matter most in daily service operations.
Data mapping through structure, not spreadsheets
A system should make it easy to understand what data exists and where it is stored. When data is spread across custom fields, uncontrolled notes, and ad hoc attachments, mapping becomes fragile. When data is structured around customers, sites, contacts, assets, and work orders, mapping becomes manageable.
Structured data also supports minimization. People are less likely to enter unnecessary personal details when the system guides them toward the right fields and purposes.
Clear retention rules aligned with operational reality
Field service businesses often need to keep service history for valid reasons. The goal is not deleting everything. The goal is defining what is kept, why it is kept, and for how long. A platform should support retention settings, archiving options, and safe deletion where appropriate.
Retention should be tied to purpose. For example, job records might be kept longer than marketing lists. Photos might require different handling than invoices. A one-size policy rarely fits all.
Support for data subject requests without panic
When a customer asks for access, correction, portability, or deletion, the response should not be a manual hunt across systems. A platform should help identify relevant records quickly and support controlled action.
The key is balance. You must respect rights without compromising required operational history or legal obligations. That requires good data structure and clear controls.
Device and mobile controls that acknowledge field reality
Mobile is where field service happens. That means GDPR compliance must function on mobile too.
A good system supports secure login, session handling, and controlled offline behavior. It reduces unnecessary local storage. It supports revocation when devices are lost. It limits what can be downloaded. It keeps job data in the platform instead of pushing teams into unmanaged messaging apps.
Vendor and subcontractor access that is limited by design
Many service businesses rely on partners. That is normal. But partner access must be controlled.
A platform should allow subcontractors to see only assigned work, not entire customer lists. It should support separate roles, separate permissions, and traceable actions. It should also support clean on-boarding and offboarding so access does not linger after contracts end.
Audit trails that are usable, not just technical logs
Audit trails should be readable and helpful. The goal is not collecting data for the sake of it. The goal is answering questions quickly and proving accountability.
When audit logs can be filtered by customer, user, event type, and timeframe, they become operational tools. When they are too technical or fragmented, they become unusable during real pressure.
The human side of GDPR that service companies cannot ignore
Technology reduces risk, but people still matter. Field teams handle customer information daily. They write notes, take photos, and communicate on-site. Small habits can create big compliance outcomes.
That is why policies and training need to be practical and short. Long documents rarely change behavior. What works better is clear rules tied to real situations.
Do not store personal information in free-text notes unless it is necessary.
Avoid capturing faces in photos unless required.
Do not share customer details over unmanaged channels.
Report lost devices immediately.
Use approved apps only.
Keep devices locked when not in use.
These actions are not about bureaucracy. They protect the technician as well as the company. When the rules are simple and supported by the platform, compliance becomes normal.
GDPR compliance as a trust advantage in service contracts
Customers increasingly expect service providers to demonstrate control over data. This is common in tenders, renewal discussions, and supplier reviews. Compliance is not only about avoiding penalties. It is about proving maturity.
When you can show structured access control, audit readiness, controlled mobile workflows, and clear retention practices, you reduce friction in deals. You also reduce internal risk. Customers trust providers that are predictable and disciplined.
For Wello Solutions customers, the advantage is that GDPR compliance can be approached as operational design. When work orders, assets, customers, and mobile execution are managed in a controlled platform, compliance becomes easier to maintain over time.
A realistic way to start without overcomplicating it
If you want to strengthen GDPR compliance in a service organization, start with the operational core.
Identify where personal data lives today.
Reduce uncontrolled storage in notes, files, and external channels.
Define roles and limit access based on real job needs.
Enable strong authentication and device controls.
Ensure you have logging and traceability.
Set retention rules that match operational and legal needs.
Train teams with short field-relevant guidance.
Make incident response clear and rehearsed.
Then build from there. Compliance improves through iteration, not through one big project.

Wello helps protect your data
Final thought: the best GDPR approach looks like good operations
GDPR compliance can feel intimidating when it is treated as a legal mountain. For service businesses, the most effective approach is to treat it as operational discipline.
Structured data. Controlled access. Traceability. Secure mobile workflows. Clear retention. Practical habits.
When these basics are in place, compliance becomes something you can maintain calmly, even as the business grows. It becomes part of how you run service at scale, not a separate effort that competes with daily performance.
And that is the real goal. Protect customer data, protect the business, and keep service moving, with confidence, every day.
A realistic way to start without overcomplicating it
If you want to strengthen GDPR compliance in a service organization, start with the operational core.
Identify where personal data lives today.
Reduce uncontrolled storage in notes, files, and external channels.
Define roles and limit access based on real job needs.
Enable strong authentication and device controls.
Ensure you have logging and traceability.
Set retention rules that match operational and legal needs.
Train teams with short field-relevant guidance.
Make incident response clear and rehearsed.
Then build from there. Compliance improves through iteration, not through one big project.